Authentication vs Authorization
-
Authentication → Who are you? (identity)
-
Authorization → What can you access? (permissions)
🔹 Challenge in Microservices
-
Multiple services
-
Stateless REST APIs
-
Shared security logic
-
Avoid session replication
👉 Solution: Token-based security (JWT + OAuth2)
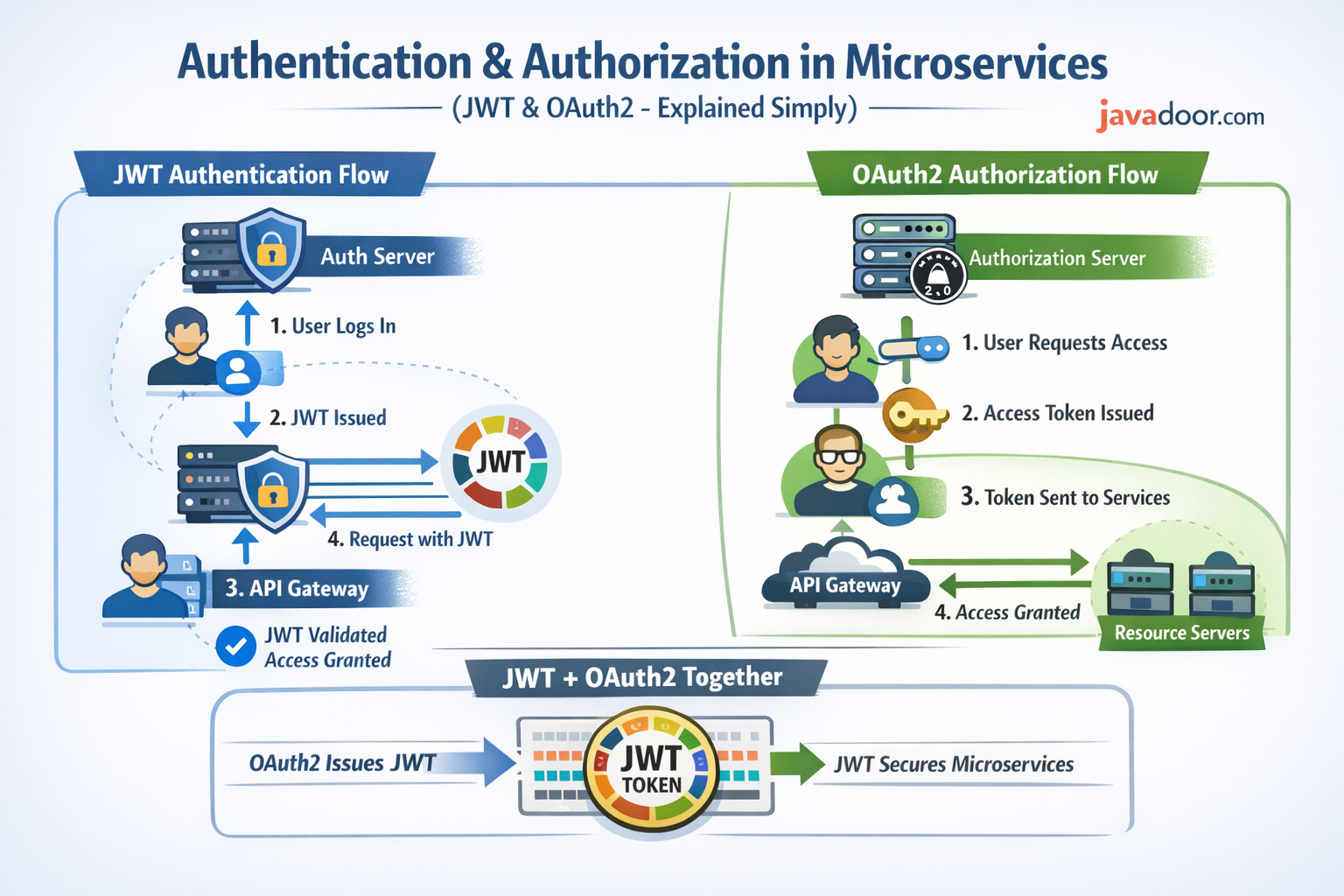
🔹 OAuth2 (High-Level)
OAuth2 is a delegation framework:
-
User authenticates once
-
Gets an access token
-
Token is used to access services
📌 Components:
-
Authorization Server
-
Resource Server (Microservices)
-
Client (UI / App)
🔹 JWT (JSON Web Token)
JWT is a self-contained token that includes:
-
User info
-
Roles
-
Expiry
-
Signature
📌 Structure:
🔹 Authentication Flow (Step-by-Step)
-
User logs in
-
Auth Server validates credentials
-
Auth Server generates JWT
-
Client sends JWT in
Authorizationheader -
API Gateway validates token
-
Request forwarded to microservice
-
Microservice authorizes based on roles
🔹 Where Security Logic Lives?
| Component | Responsibility |
|---|---|
| API Gateway | Token validation, rate limiting |
| Auth Server | Login, token issuing |
| Microservices | Role-based access |
🔹 Spring Security Example
🔹 Advantages
✅ Stateless
✅ Scalable
✅ No session storage
✅ Works well with microservices
🔹 Challenges
❌ Token revocation is hard
❌ Token expiry handling
❌ Key rotation
🔹 Best Practices
-
Short-lived access tokens
-
Refresh tokens
-
Validate JWT at API Gateway
-
Use HTTPS always
⭐ Interview One-Liner
“Microservices typically use OAuth2 with JWT for stateless, scalable authentication and role-based authorization.”
🔹 Follow-Up Questions
-
JWT vs Session?
-
How do you revoke JWT?
-
Where do you store refresh tokens?
